Hiding in plain sight has many dimensions. Sometimes, whatever you are looking for is before you, but you cannot see it; other times, it’s right before you but you don’t notice.
Steganography has been an art since the ancient days used to write hidden messages. It has evolved over the ages, and has changed form for the better. Nowadays we have software to hide and obfuscate messages. In this article, we’ll take a look at some amazing steganographic tools which are tiny yet powerful.
Steghide
Steghide is one of the most popular steganographic tools out there. It comes preinstalled in some of the GNU/Linux distributions. If it’s not installed, you can download it from your package manager or you can check their Github. It can hide data inside images and audio files, it supports JPEG, BMP, WAV and AU formats.
Let’s create a text file named secret.txt and try to hide it inside an image.

steghide embed -cf yoda.jpg -ef secret.txt
Here -cf is cover file and -ef is embed file. The caveat is, you should make sure your cover file is larger than your embed file, that’s a no brainer.
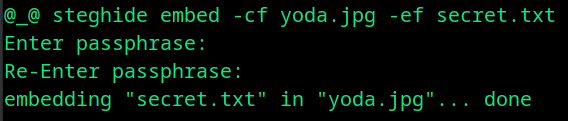
Now let’s delete the secret.txt and see if we can extract it back from the cover file.
steghide extract -sf yoda.jpg
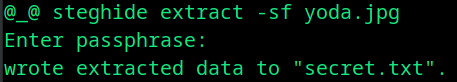
Here the -sf is stego file.

Our secret.txt is extracted. Wanna see what’s inside?
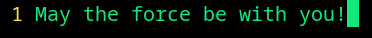
Strings
Let’s digress from the topic a bit. Strings is a command line tool that helps to display printable strings in a file. In a sense, it’s just like cat command. If you didn’t know already, now it’s a chance to explore it.
strings can be super helpful in steganographic challenges. For instance, let’s say, a flag or password is embedded inside an image file. And you have to match or put printable strings together in order to solve the challenge.
If you cat out the file, you will end up with gibberish characters printed out on to your screen.
cat yoda.jpg

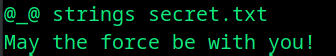
Whereas, if you use strings, you’ll get a bunch of strings with printable characters.
strings yoda.jpg
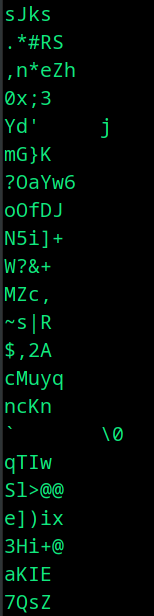
Among them, one of it might be your password or flag or a clue to the next stage.
Exiftool
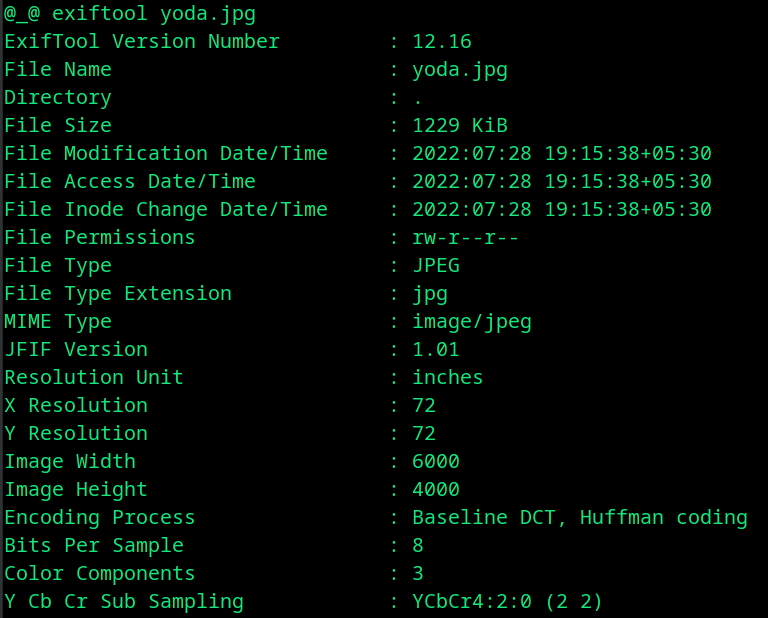
Exif is a good place to hide your secret message. Exiftool helps to view the information about metadata of images or files. Besides, embedding secret messages, exif data could provide some juicy information about the image, such as, geo coordinates, camera model, creation date and so on. You can use simple tools like gThumb or GIMP to edit medtadata.
exiftool yoda.jpg
Binwalk
Binwalk is a tool for searching binary images for embedded files and executable code. It is actually a forensic tool, which helps to analyse and audit binaries. It gives plenty of options to tinker around binary files. Let’s see couple of options.
Here we have source code of a web page.
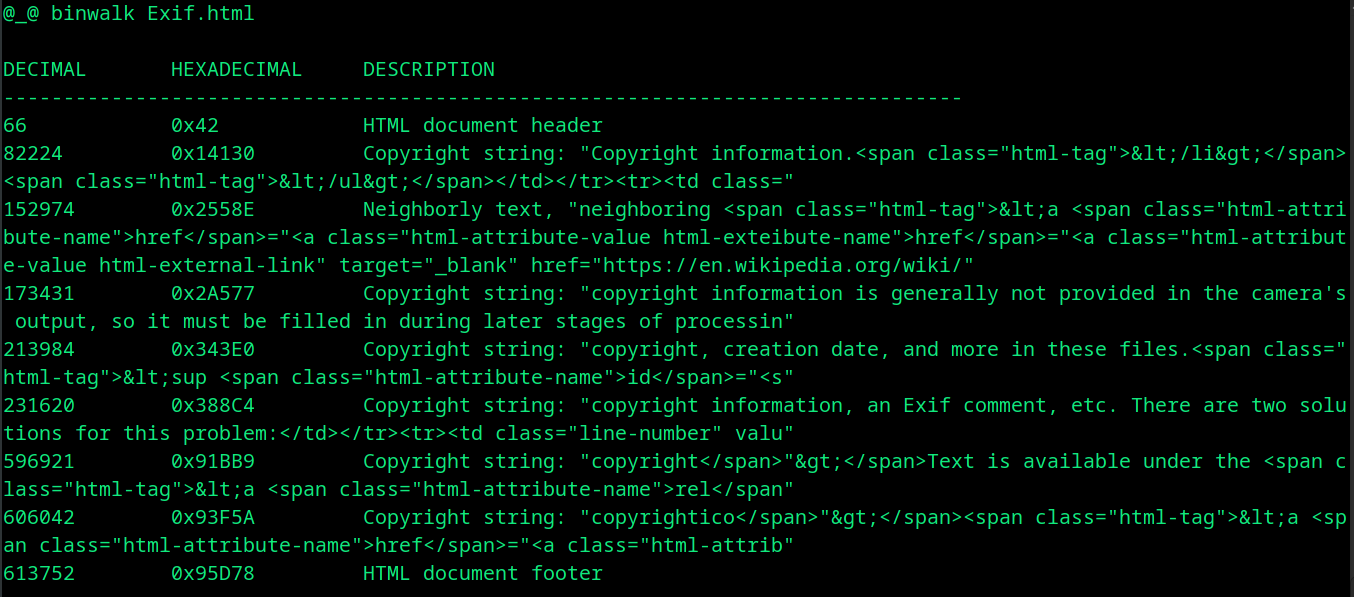
It just displays the embedded data in a given file. If you want to extract the data from a binary, use -e flag.
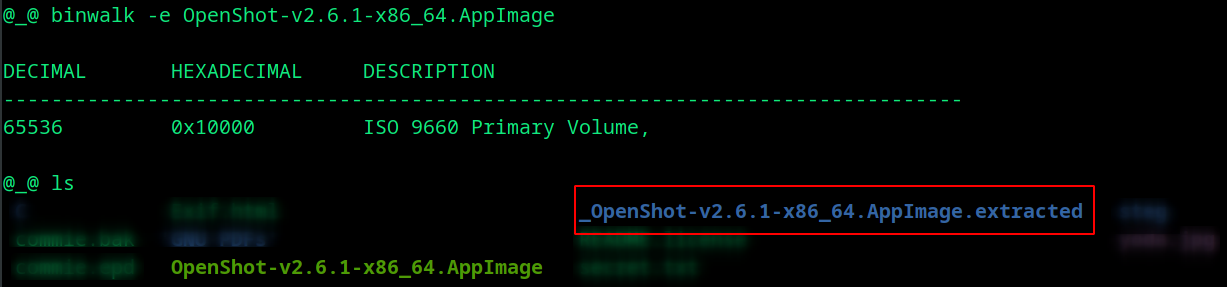
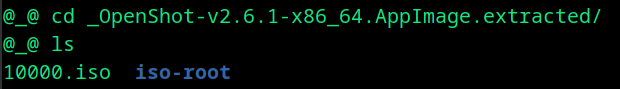
The file is extracted to _OpenShot-v2.6.1-x86_64.AppImage.extracted folder.
Wavsteg
WavSteg is a tool written in Python, which can hide data in files with a wav format.
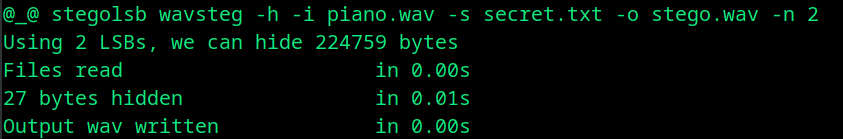
stegolsb wavsteg -h -i piano.wav -s secret.txt -o stego.wav -n 2
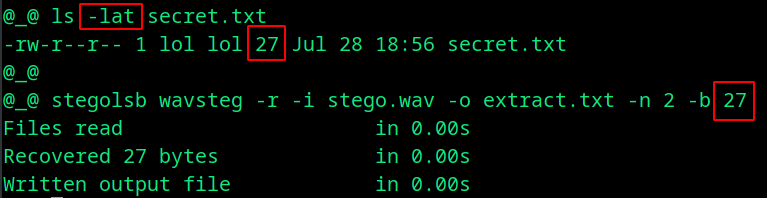
While extracting data, you have to specify the exact size of embedded file(secret.txt) in bytes
Other Useful Resources
There are many online tools and professional software that could facilitate steganography. Some of them are in the following.